Network Management for Today’s Changing Workforce
Fortify NMS
Fortify NMS is a secure cloud-based network management and monitoring service designed to deploy in minutes.
Our lightweight collector immediately begins discovering network devices and collecting valuable network data as soon as it’s done.
Only pay for routers, switches, firewalls, wireless AP controllers, all other devices are included for free.
Stay consistent across your equipment with device-agnostic programming.
Increase your efficiency with automated network discovery, inventory and backups.
Know when the network changes thanks to pre-configured and customizable alerts.
See when stray devices and network loops appear with real-time mapping.
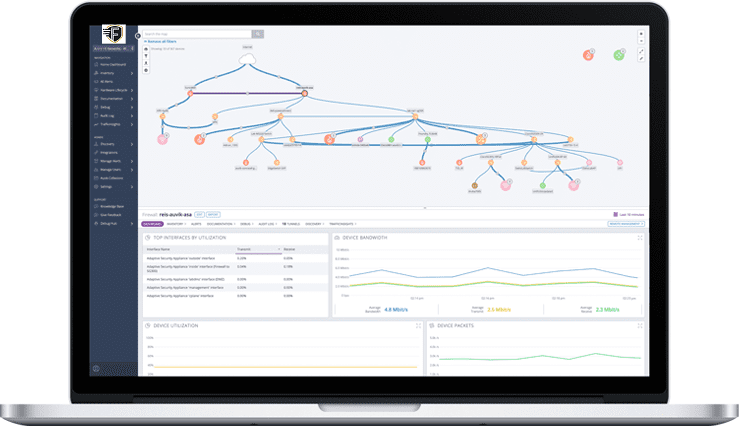
A complete network picture in minutes with automated mapping, inventory, and documentation
The days of wire tracing, port mapping, and reverse engineering network connections based on VLAN or IP assignments are over. Fortify NMS automates network discovery to give you complete network visibility and control—and it keeps all of your information up to date as the network evolves … one less thing to wory about.
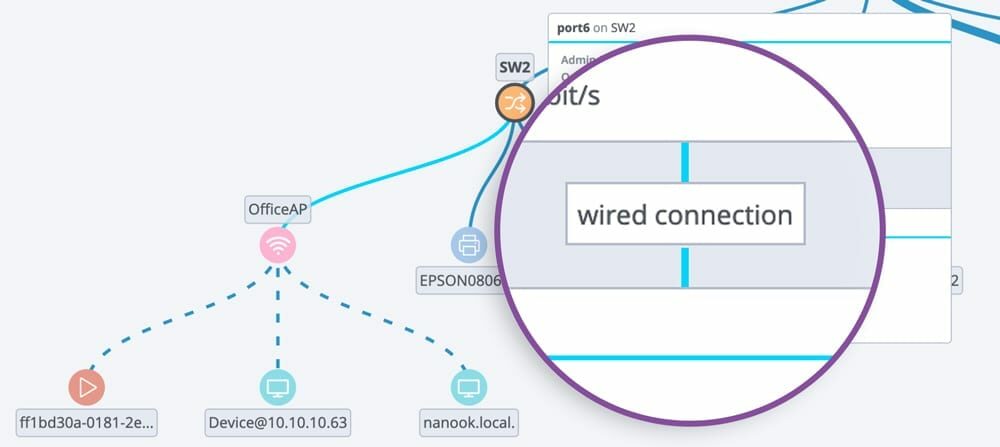
Know what’s on your network and how it’s all connected in real-time
Fortify NMS pulls data from CDP, LLDP, and forwarding tables to model the Layer 1 network diagram. Layers 2 and 3 are built from ARP tables, IP assignments, and VLAN associations to show you exactly what’s on the network, where it is, and how it’s connected.
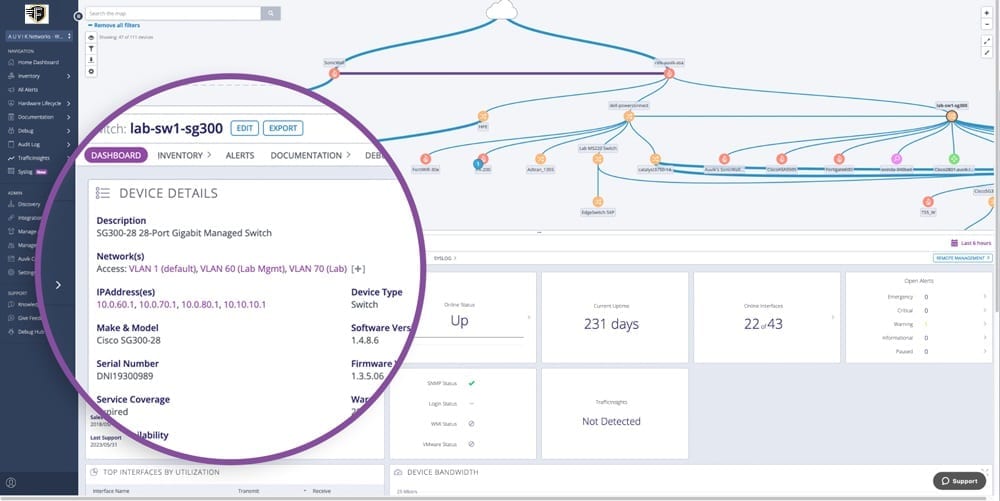
Full details for every device on the network
Fortify NMS automated inventory leverages network protocols to detect and capture full details for every device on the network including their make and model, serial number, IP address, and the physical switchport the device is connected to. Easily find any device you’re looking for and every other device it’s connected to.
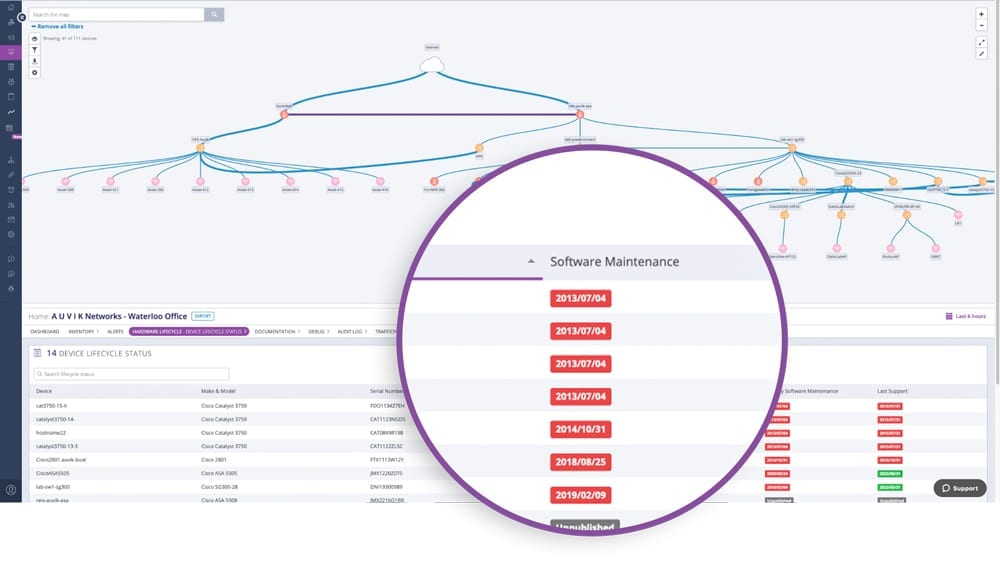
Identify which devices need to be upgraded or replaced
Fortify NMS uses lifecycle data retrieved from supported devices to show whether they’re on current or expired support contracts, whether there are more up-to-date software versions available, if devices are eligible to receive critical security updates, and if devices are still available for purchase.
Real-time respond to network issues, protect users from unnecessary downtime and monitor application traffic.
Fortify NMS streamlines and simplifies network monitoring and troubleshooting to help you keep your users connected to business critical resources. Fortify NMS backs up and maintains configuration for each eligible network devices is. Fortify NMS supports NetFlow v5, NetFlow v9, J-Flow, IPFIX, or sFlow to show you who’s on the network, what they’re doing, and where their traffic is going even when the traffic’s encrypted.
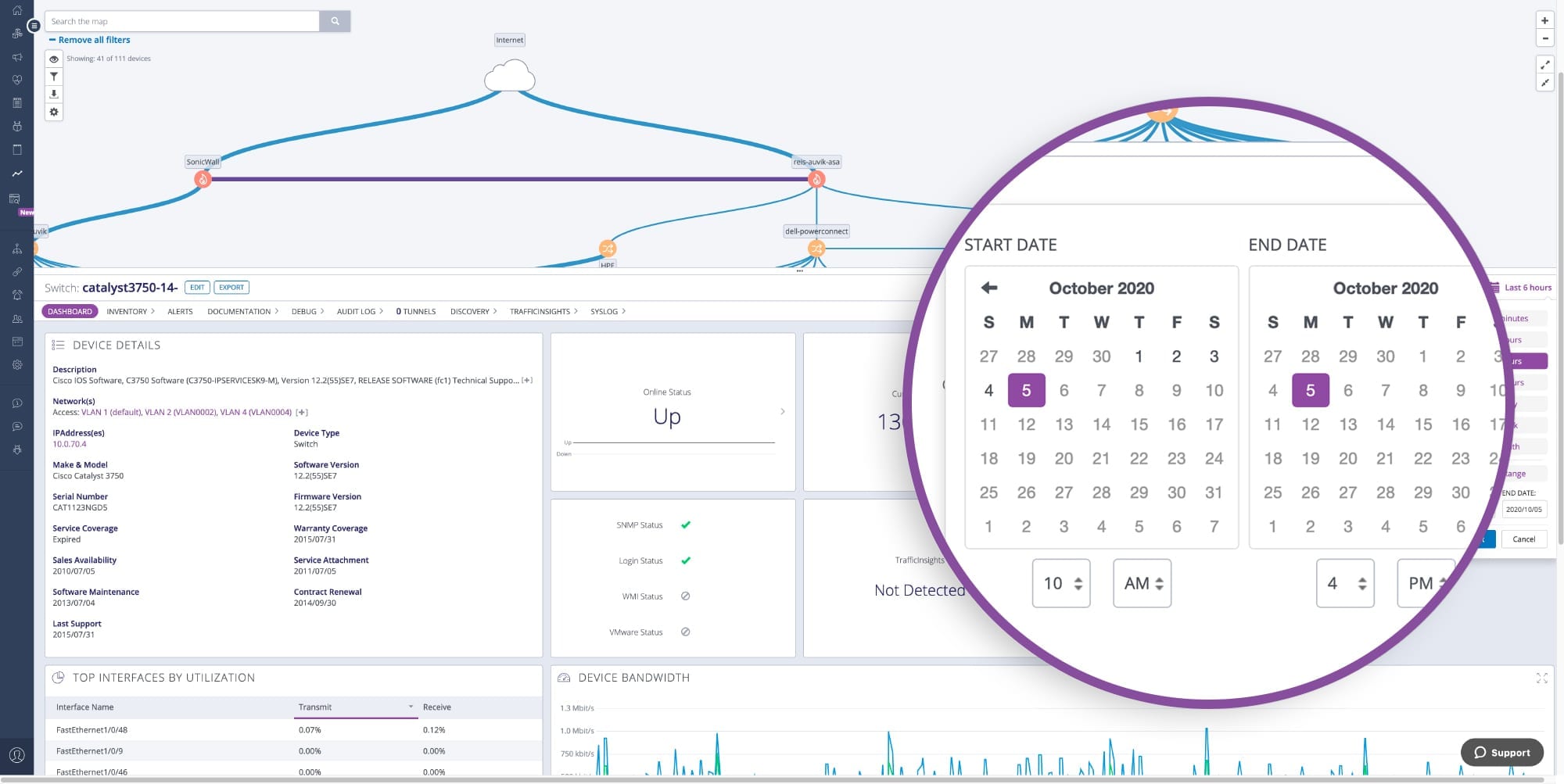
Real-time metrics and historical data
Fortify NMS is constantly monitoring and polling your network to give you a real-time look at your network at a single point in time. The network data Fortify NMS detects is stored for years, providing a rich archive for troubleshooting, analysis, planning, and reporting.
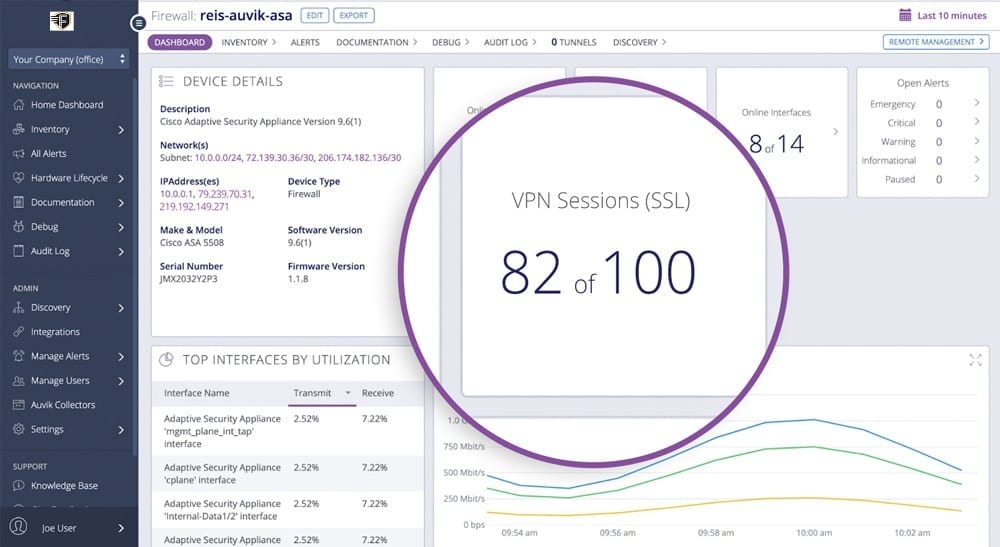
Support Your Remote Workers by Preventing VPN Capacity Issues
Ensuring remote workers are able to acces the firewall based SSL VPN is more important now than ever. Fortify NMS can show you instantly how many VPN sessions are in use and if you’re approaching your license limit.
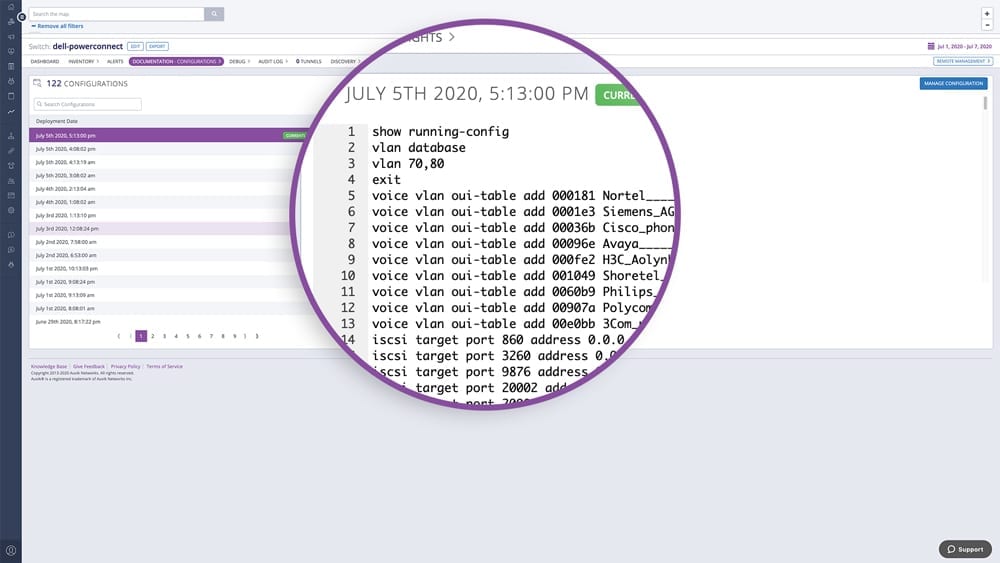
Up-to-date device configs directly at your fingertips
Fortify NMS scans network devices for configuration changes every 60 minutes. If a device’s running config has been altered, the latest config is automatically backed up. The old config gets logged into a version index that’s always available for review. Select any configuration in a device’s version history and immediately see which configuration elements have been added, edited, or removed with an easy color-coded system.
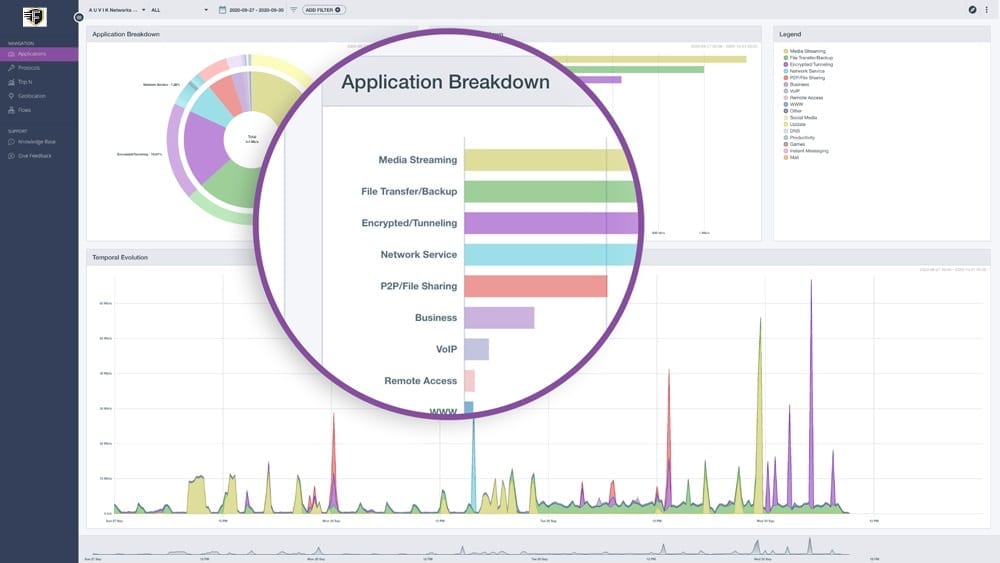
Ensure business critical applications have required bandwidth
Fortify NMS utilizes machine learning and traffic classification to show you which applications are consuming bandwidth and helps identify shadow IT services like Google Drive, Box, Dropbox. Fortify’s support team will notify you if additional bandwidth needs to be purchased to support your organizations needs.
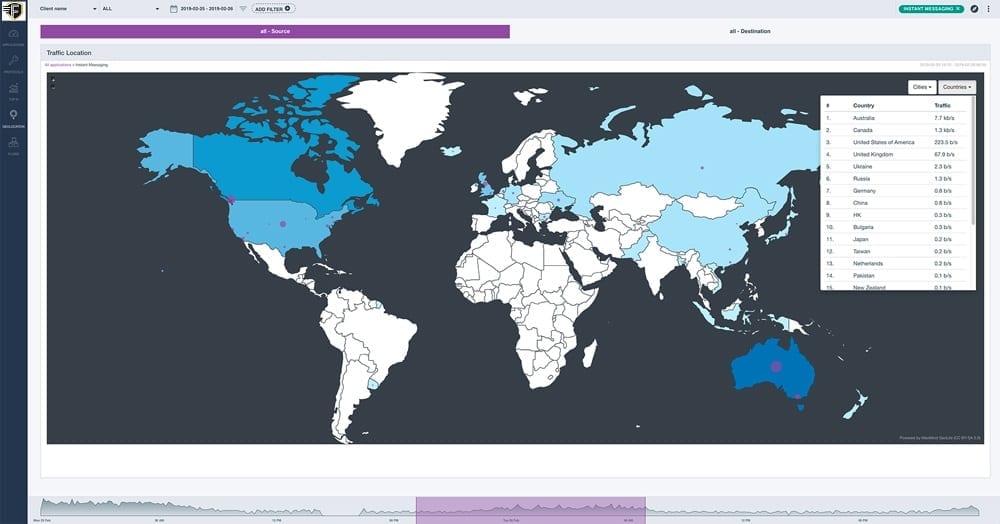
Know exactly where traffic is going when it leaves the network
Fortify NMS displays real-time traffic source and destination data in a simple world map. Identify traffic received from or delivered to blocked countires, command & control (C2) for malware and botnets. Verify traffic by reviewing the flow records to ensure your confidential data is secure.